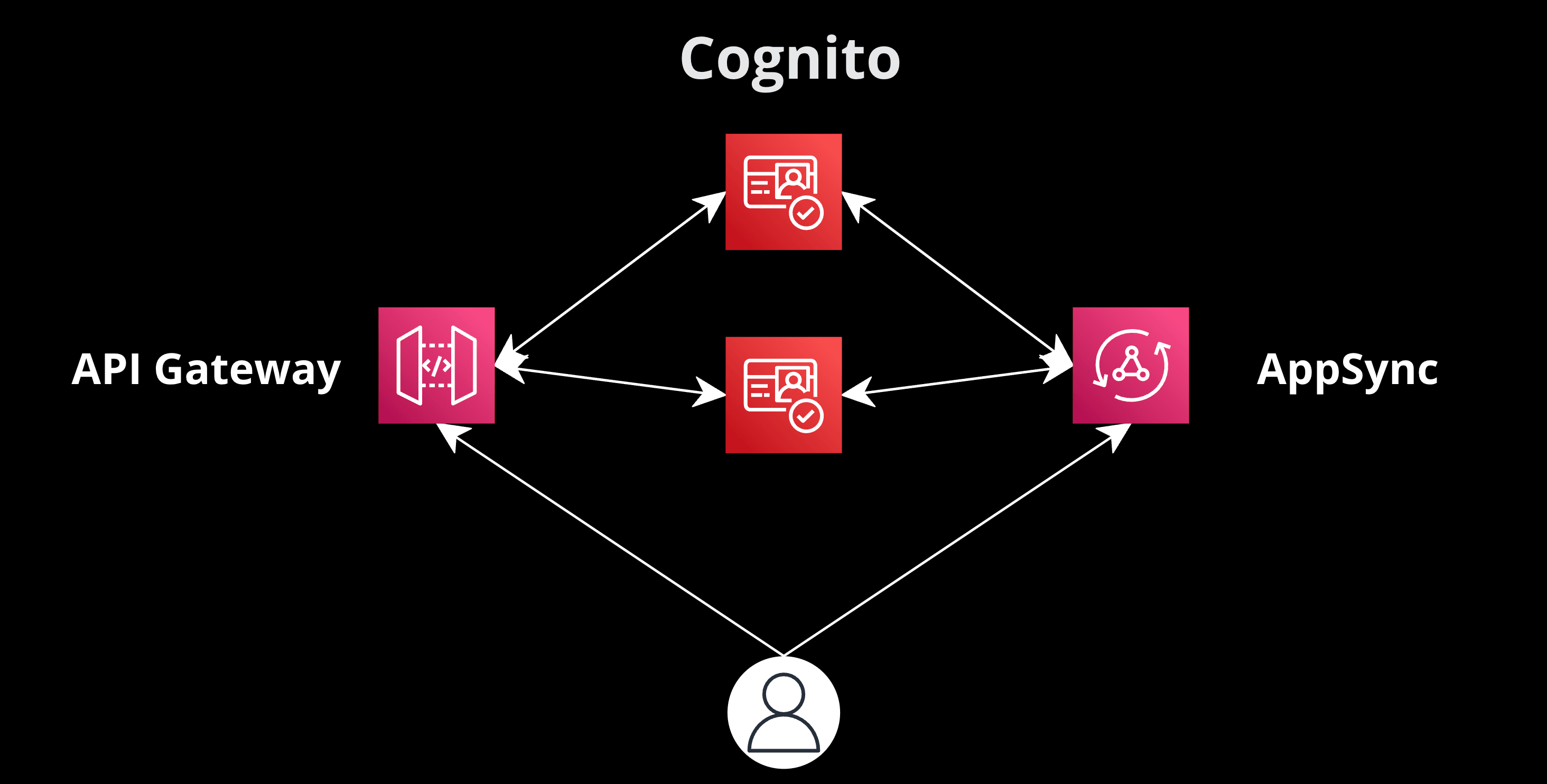
This is a series of articles about setting up a complex Serverless backend infrastructure with AWS SAM and CloudFormation.
Here is the index of all the articles in case you want to jump to any of them:
1. Setup of AppSync and API Gateway with Multiple AWS Cognito User Pools
2. Configuring S3 Buckets with Permissions and Access Roles in AWS Cognito AuthRole
3. Intro to DynamoDB Resolvers for AppSync Implementation
4. Intro to Lambda Resolvers for AppSync Implementation
5. Configuring an AWS VPC to Include Lambda Resolvers with a Fixed IP
6. Intro to Pipeline Resolvers for AppSync Implementation
7. Handling Lambda Resolver Timeouts with SNS Messages
Introduction
AWS AppSync and API Gateway are powerful tools in the AWS ecosystem. When combined with AWS Cognito User Pools, they offer a robust authentication and authorization mechanism. This guide will delve into setting up AppSync and API Gateway with two distinct Cognito User Pools: one for general users and another for back-office operations.
For a deeper dive into Congito Configuration, please refer to my previous article: Configuring Two Cognito User Pools for a Single AppSync GraphQL API: A YAML CloudFormation Template Guide
Why Two User Pools?
Having two separate user pools clearly distinguishes between general users and back-office staff. This separation ensures that each group has tailored permissions, enhancing security and operational efficiency.
The code
Setting Up AppSync with Multiple User Pools
- Create Two Cognito User Pools: Start by setting up two distinct user pools in AWS Cognito. Name them appropriately to avoid confusion.
- Integrate with AppSync: Setup the CloudFormation resource and link it with the two Cognito User Pools
Resources:
# Cognito User Pools
UserPoolGeneral:
Type: "AWS::Cognito::UserPool"
Properties:
UserPoolName: "GeneralUsers"
Schema:
- Name: email
AttributeDataType: String
Mutable: true
Required: true
AutoVerifiedAttributes:
- email
UserPoolBackoffice:
Type: "AWS::Cognito::UserPool"
Properties:
UserPoolName: "BackofficeUsers"
Schema:
- Name: email
AttributeDataType: String
Mutable: true
Required: true
AutoVerifiedAttributes:
- email
# AppSync API
AppSyncAPI:
Type: "AWS::AppSync::GraphQLApi"
Properties:
Name: "MyAppSyncAPI"
AuthenticationType: "AMAZON_COGNITO_USER_POOLS"
UserPoolConfig:
UserPoolId: !Ref UserPoolGeneral
AwsRegion: !Ref "AWS::Region"
AdditionalAuthenticationProviders:
- AuthenticationType: "AMAZON_COGNITO_USER_POOLS"
UserPoolConfig:
UserPoolId: !Ref UserPoolBackoffice
AwsRegion: !Ref "AWS::Region"
AppSyncSchema:
Type: "AWS::AppSync::GraphQLSchema"
Properties:
ApiId: !GetAtt [AppSyncAPI, ApiId]
Definition: |
type Query {
getData: String
}
schema {
query: Query
}Configuring API Gateway
- Create Resources: Create resources representing your application's endpoints.
- Set Authorization: For each resource, set the authorization to AWS Cognito and select the appropriate user pool.
Resources:
# ...
# API Gateway
MyApi:
Type: 'AWS::ApiGateway::RestApi'
Properties:
Name: 'MyAPI'
Description: 'My API service.'
FailOnWarnings: 'true'
RootMethod:
Type: 'AWS::ApiGateway::Method'
Properties:
AuthorizationType: 'COGNITO'
AuthorizerId: !Ref CognitoAuthorizer
HttpMethod: 'ANY'
ResourceId: !GetAtt [MyApi, RootResourceId]
RestApiId: !Ref MyApi
CognitoAuthorizer:
Type: 'AWS::ApiGateway::Authorizer'
Properties:
Name: 'CognitoAuthorizer'
IdentitySource: 'method.request.header.Authorization'
RestApiId: !Ref MyApi
Type: 'COGNITO_USER_POOLS'
ProviderARNs:
- !GetAtt [UserPoolGeneral, Arn]
- !GetAtt [UserPoolBackoffice, Arn]Conclusion
Businesses can ensure a secure and organized authentication system by setting up AppSync and API Gateway with multiple AWS Cognito User Pools. This setup is especially beneficial for applications that need to differentiate between general users and administrative staff.
Please note that the code examples have been simplified to help understand the approach and the resources. Some adjustments might be needed.
---------
Next UP: Part 2. Configuring S3 Buckets with Permissions and Access Roles in AWS Cognito AuthRole